In accordance with Department of Defense Directive (DoDD) 5105.65, “Defense Security Cooperation Agency,” Chapter 13 Security Cooperation (SC) Information Technology (IT) Systems provides guidance to the SC community on the management of DSCA-funded IT systems that support Security Assistance (SA) programs and identifies the major IT systems used by the SC community. DSCA (Office of Business Operations, Information Management and Technology Directorate (OBO/IMT)) manages these IT systems and services to support the SA community in furthering the SC mission.
Section | Title |
|---|---|
C13.1. | |
C13.2. | |
C13.3. | |
C13.4. | |
C13.5. |
C13.1.1. Mission. To provide an effective and comprehensive range of information technology (IT) mission systems and services to support DSCA and the Security Cooperation Enterprise (SCE) to continually deliver business value and further national defense and foreign policy interests.
C13.1.2. Vision. To be the trusted provider of innovative, reliable, accessible, and secure information management and technology solutions to operationalize efficiencies and empower the Security Cooperation (SC) community in defense of our nation, allies, and partners.
C13.1.3. DSCA maintains and operates information systems that support DSCA and the SC community, and develops and enhances information systems to deliver new business value to the SC community. DSCA (Office of Business Operations, Information Management and Technology Directorate (OBO/IMT)), led by DSCA’s Chief Information Officer (CIO), aligns IT strategy and policy established by the DoD CIO, Defense Information Systems Agency (DISA), and U.S. Cyber Command (USCYBERCOM) to ensure SC-wide IT development efforts, operations, and systems work in an effective, efficient, and compliant method. Further, DSCA (OBO/IMT) IT engineering and service management support is incorporated through mission-essential system capabilities and strategic planning for success of the SC enterprise.
C13.1.4. DSCA’s IT governance framework provides the overarching parameters used by the SC community IT governance board’s decision-makers to analyze, select, control, and evaluate IT investments.
C13.2.1. DSCA administers a defined, repeatable information technology (IT) investment framework by which Security Cooperation (SC) decision-makers align IT investments with business strategy to achieve specific outcomes. The framework also ensures interoperability, fiscal accountability, and compliance with DoD rules, regulations, and standards. IT governance for the SC community is required to operate within the parameters and constraints of the governance structure approved and implemented by the Secretary of Defense (SECDEF). The SC IT governance framework includes management controls that ensure the integrity of IT investments, in conjunction with senior level oversight from the Military Departments (MILDEPs), as appropriate.
C13.2.2. The IT governance framework utilizes decision making and advisory boards, to include the Portfolio Investment Review Board (PIRB) and Strategic Investment Board (SIB). These boards implement and facilitate policies and processes, optimize resource allocation and utilization, and manage SC IT portfolios through effective evaluation, selection, prioritization, and funding of IT investments. This demand-focused approach enables:
C13.2.2.1. The PIRB to endorse IT investments from a business operations perspective.
C13.2.2.2. The SIB Chair to approve IT investments from a strategic, mission, and policy perspective.
C13.2.3. Information Technology Governance Process. The IT governance process is driven by several core principles to ensure optimal performance within DSCA, an increased value to the SC community, and the reduction risk.
Table C13.T1. Core Principles of the IT Governance Process
# | Core Principle |
|---|---|
1 | Strategic Alignment: Align IT spending with DSCA’s strategic goals. |
2 | Business Value: Provide business value to the SC community through IT. |
3 | Risk Management: Identify material threats and opportunities related to the achievement of the SC’s business objectives. |
4 | Performance Management: Establish performance metrics for measuring results. |
5 | Resource Management: Optimize resource management. |
6 | Technical Advisory: Integrate IT technical advisory functions to analyze initiatives against technical standards. |
C13.2.4. Information Technology Governance Board Pyramid. The IT Governance Board pyramid portrays the decision-making hierarchy across DSCA’s governance, where each level provides recommendations, as appropriate, while also having independent responsibilities focused on evaluation and decision-making.
Figure C13.F1. Information Technology Governance Board Pyramid
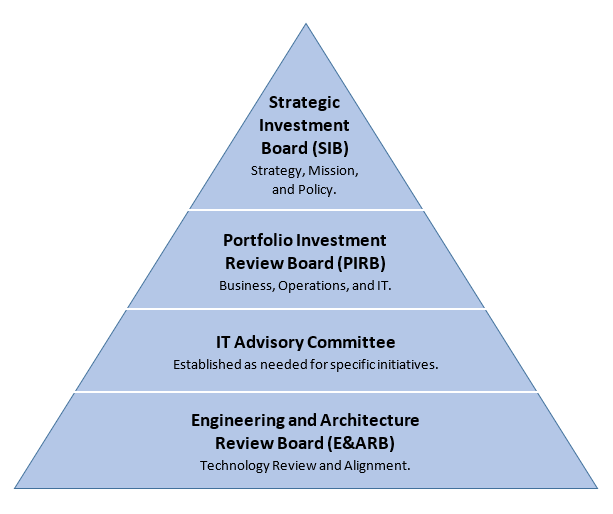
C13.2.4.1. Strategic Investment Board. The SIB governs SC portfolios of DSCA-funded IT investments by assuring investments achieve DSCA strategic objectives. The SIB is chaired by DSCA’s Assistant Director for Business Operations and includes executive-level SC enterprise functional members from across DSCA, MILDEPs, and Implementing Agencies (IAs) with equity in IT investments. The SIB’s responsibilities include:
C13.2.4.1.1. Supporting DSCA’s governance strategy to create value for the SC enterprise through integrated and hierarchical investment management decision-making.
C13.2.4.1.2. Maximizing return on investment for any risks incurred.
C13.2.4.1.3. Consistently evaluating the benefits to the enterprise during the investment’s lifecycle.
C13.2.4.1.4. Establishing organizational governance processes, and/or effect enterprise changes, as appropriate for an investment.
C13.2.4.1.5. Evaluating the cost-effectiveness, risk reduction, and benefit realization to assess the intake of new IT investments and the delivery of existing IT investments and portfolios.
C13.2.4.2. Portfolio Investment Review Board. The PIRB makes operational and tactical decisions to support approved strategy and guidance developed by the SIB. The PIRB is chaired by the DSCA CIO with members including DSCA Deputy Assistant Directors and equivalent representatives from the MILDEPs who hold decision-making authority for IT investments and operational expertise to advise the SIB. The PIRB’s responsibilities include:
C13.2.4.2.1. Providing counsel to the SIB on IT investments in support of DSCA’s governance strategy.
C13.2.4.2.2. Providing the SIB with recommendations and endorsements focused on the integration of business operations and IT services to improve integration of IT systems to support the SC enterprise.
C13.2.4.2.3. Providing portfolio level expert advice from their respective functional area leveraging the technical feasibility analysis and recommendations from Advisory Committees’ evaluations.
C13.2.4.3. Information Technology Advisory Committees. IT Advisory Committees are established on an as needed basis and provide the governance boards with subject matter expertise in the review of and advice on specific subjects such as technical requirements, enterprise data, business architecture, and impacts of system changes. Subject matter experts across the SC community provide IT Advisory Committees with pertinent IT investment information focused on technical feasibility through assessment and evaluation.
C13.2.4.4. Engineering and Architecture Review Board. Chaired by DSCA’s Chief Technology Officer (CTO) within DSCA (OBO/IMT), the Engineering and Architecture Review Board (E&ARB) is an internal DSCA team that provides IT expertise to the IT Advisory Committees, Chief Information Officer (CIO), PIRB, and SIB. The E&ARB provides strategic engineering and architectural guidance for core IT systems across the SC community, to include those managed by the MILDEPs. The E&ARB, through its review, ensures SC-wide systems and applications are worthwhile investments, while promoting compliance with DoD and DSCA IT policies and procedures, Enterprise Architecture, and IT infrastructure standards and guidelines.
C13.2.5. Information Technology Investment Thresholds. SC-specific tiers are established for IT investment requests within business system category (BCAT) III, to include the required approval authority within the IT investment framework for each tier. In accordance with Department of Defense Instruction (DoDI) 5000.75 “Business Systems Requirements and Acquisition”, BCAT I and BCAT II requests are approved externally to DSCA as identified below.
Table C13.T2. Business System Category Thresholds
Investment | Criteria | Decision |
|---|---|---|
BCAT I |
| DoD CIO |
BCAT II |
| DoD CIO/ MILDEP Chief Management Officer (CMO) |
BCAT III* |
| SIB |
BCAT III* |
| PIRB |
BCAT III* |
| DSCA CIO |
*Approval of BCAT III requirements by the DSCA CIO, PIRB, and/or SIB does not authorize funding. Additional information on funding approval processes can be found in Chapter 14. | ||
C13.2.6. Intake to Prioritization Process.
C13.2.6.1. DSCA utilizes the centralized Intake to Prioritization (I2P) Process to align IT projects and demands through a vetting and prioritization process to improve consistency and efficiency across the SC community. IT project requests received by DSCA go through I2P’s comprehensive six-phase protocol to ensure all IT projects are subject to, and meet, standards established by the DSCA CIO.
Table C13.T3. Intake to Prioritization Process
Phase | Process |
|---|---|
1: Intake | This phase initiates the DSCA (OBO/IMT) I2P Process by determining if a request is complete, it is duplicative, or should be redirected to the DSCA (OBO/IMT) Service Desk. New requests must be submitted utilizing the “Drive Innovation” link on DSCA’s Service Portal. |
2: Engage | DSCA engages with the requestor to begin development of the business requirements package. DSCA also assesses initial technical feasibility and alignment with existing tools. |
3: Acceptance | Through the E&ARB review, DSCA verifies that the request is technically feasible and within DSCA’s (OBO/IMT) scope. DSCA also determines if the request is to be resolved with DSCA resources or outsourced. |
4: Solution Analysis | DSCA develops courses of action to fill the business requirements and provides inputs for approval and/or submission to the IT Governance Boards. |
5: Governance | DSCA ensures that all IT requests requiring PIRB or SIB review are submitted appropriately. |
6: Project Prioritization | DSCA collects all Subject Matter Expert (SME) approvals and governance decisions, creating and prioritizing an official DSCA (OBO/IMT) project on the OBO/IMT project list. Once a demand completes Project Prioritization it becomes a Project and enters DSCA’s Software Development Lifecycle (SDLC). |
C13.3.1. DSCA funds, operates, and maintains information systems to support the execution of Security Cooperation (SC) organizational capabilities and activities. Additionally, DSCA funds and maintains information systems utilized by the Military Departments (MILDEPs) and Implementing Agencies (IAs) to process Foreign Military Sales (FMS) cases. To assist in the effective development and sustainment of investments, programs, projects, and systems across the SC community DSCA (Office of Business Operations, Information Management and Technology Directorate (OBO/IMT)) employs the below SC information technology (IT) portfolios. The DSCA Chief Information Officer (CIO) is responsible for reviewing any proposed new systems or system changes within the SC community to maintain the IT processes and cost efficiencies. Each IT system is managed either by DSCA or the appropriate IA and require appropriate permissions for access. Tier 1 and Tier 2 systems funded by DSCA are grouped within their respective portfolio, as follows. This section does not include IT systems that control and distribute funds for the MILDEPs and IAs.
C13.3.2. Enterprise Decision Support. These IT systems include analytical and rule-based systems that provide an enterprise approach to applying multiple data-based capabilities to assess, plan, execute, monitor, and evaluate operations.
C13.3.2.1. Security Cooperation Common Operating Picture. The Security Cooperation Common Operating Picture (SC-COP) supports strategic decision-making and a full-spectrum approach by integrating all the necessary information and data to provide data reporting and visualization capabilities for the full life cycle of security cooperation programs, including both grant security sector assistance and FMS.
C13.3.2.1.1. SC-COP is hosted in DoD’s ADVANA platform and coordinates reporting, data visualization, and dashboard requirements from three streams of work:
- Case lifecycle data within the Case Lifecycle Management Suite (CLMS);
- Non-FMS program and activity lifecycle data, including strategic planning, program and activity design, and Assessment, Monitoring, and Evaluation (AM&E); and
- Other Agency data requirements that fall outside the scope of the above two categories (e.g., Weapons Systems Analysis requirements).
C13.3.2.1.2. SC-COP does not replace existing reporting capabilities in legacy systems. Defense Security Assistance Management System (DSAMS) and other legacy systems retain and enhance functionality needed to provide users with immediate up-to-date case lifecycle information for development, execution, and reporting purposes.
C13.3.2.2. Socium. Socium is the DoD enterprise-wide system of record for SC program design, planning, budgeting, assessment, monitoring, evaluation, and reporting in support of all U.S. SC initiatives and legal-authority based activities to include the integration of Title 10 and Title 22 programs. Socium maintains automated inbound data interfaces with Combatant Command (CCMD) SC systems and Security Cooperation Information Portal (SCIP); inbound/outbound interfaces with SC authoritative data sources including DSAMS and Command Control Information Environment (C2IE); and outbound data interfaces with its custom ArcGIS instance and ADVANA to provide SC workflow management, Global Campaign Plan to SC Initiative and Partner Nation Role association, Activity-to-case integration, and geographic data-visualization. Socium (up to CUI) is accessible on non-DoD networks for all DoD and Department of State (State) military, civilian, and contractor personnel and is available up to the Secret level on DoD Secret Internet Protocol Router Network (SIPRNet). Socium operates under an iterative and continuous improvement development framework with releases every six to nine weeks allowing the SC enterprise to inform requirements, set priorities, and tailor Socium to SC policy requirements and user-specific enhancements.
C13.3.3. Case Development. These IT systems include those that provide the means for the SC community to develop and establish SC cases.
C13.3.3.1. Defense Security Assistance Management System. The DSAMS is a DoD system used for the development and implementation of all unclassified cases for FMS, Building Partner Capacity (BPC), International Military Education and Training (IMET), and other aspects of SC involving the transfer of defense articles, services or training, through sale, grant or lease, to allied and friendly foreign partners and international organizations under the authority of the Arms Export Control Act (AECA), the Foreign Assistance Act (FAA), and other laws and regulations.
C13.3.3.1.1. Defense Security Assistance Management System - Training Module. The DSAMS Training Module (DSAMS-TM) is the system of record to program, manage, execute, and track the SC International Military Student (IMS) training program and associated financial management. This includes the training of foreign personnel authorized under the FAA for IMET, as amended, and the AECA for FMS training, as amended. Traditional IMET and FMS authority is limited to training military and civilian personnel for the host nation defense establishment. Legislation for expanded IMET provides authority to train defense and non-defense personnel with emphasis on civilians from other government agencies and legislators involved in defense matters. DSAMS-TM is utilized by each MILDEP training activity at varying levels to manage training for FMS cases, IMET, and other training programs.
C13.3.4. Case Execution. These IT systems include those that provide the means for the SC community to execute security cooperation cases in accordance with applicable policies required for delivery of defense articles, services, and trainings.
C13.3.4.1. Centralized Integrated System for International Logistics. The U.S. Army utilizes the Centralized Integrated System for International Logistics (CISIL) for the management of FMS cases. The system maintains data from country request to FMS case closure. It also produces logistics requisitions (e.g., Military Standard Requisitioning and Issue Procedures (MILSTRIP)), case status, status of delivery, repair status, supply discrepancy status, and other management reports.
C13.3.4.2. Case Management Control System. The U.S. Air Force utilizes the Case Management Control System (CMCS) to provide financial and logistical tracking of FMS cases. CMCS provides for the creation and maintenance of case file data related to FMS cases for case planning, execution, and management. This central collection point performs unique FMS accounting functions in real-time with on-line interactive financial management capabilities and updating/reporting operations that interface with other systems during the life of a case. Such functions include obligation authority, commitments, expenditure authority, disbursement of funds, customer billing, total financial reporting, case oversight and delivery of goods made on FMS cases including line and case closure.
C13.3.4.3. Defense Integrated Financial System. The Defense Integrated Financial System (DIFS) is the interfacing accounting system which links implementing activity records with the bill (DoD Form 645) and supporting financial documents issued to FMS purchasers for the procured defense articles and/or services. IA Case Managers must track the financial status of the FMS cases for which they are responsible throughout the execution phase as well as throughout the entire life span of the case. Anomalies in the DIFS output must be reviewed and reconciled by the Case Manager with the intended provisions of the case. DIFS provides Case Managers with one tool showing the visibility of the financial configuration of their cases in the accounting system at Defense Finance and Accounting Services - Indianapolis (DFAS-IN) from the offered stage through case closure and beyond. DIFS verifies that computations are being made in accordance with FMS cases. DIFS also provides “real time” data to Case Managers for country programs analysis and for summary reports to the FMS purchasers and within their activity.
C13.3.4.4. Management Information System for International Logistics. The U.S. Navy utilizes the Management Information System for International Logistics (MISIL) system to manage the execution and accounting of all FMS cases. MISIL maintains data from country request to FMS case closure. The system processes, controls, tracks, and reports on FMS logistics and financial transactions, including requisitions, acquisitions, supply/delivery status, Supply Discrepancy Reports (SDR), and expenditures. MISIL is the official accounting system of record for all Navy FMS and produces logistics requisitions (e.g., MILSTRIP), case status, status of delivery, repair status, supply discrepancy status, and other management reports.
C13.3.4.5. Security Assistance Management Information System. The U.S. Air Force utilizes the Security Assistance Management Information System (SAMIS) to process logistical and financial data on U.S. Air Force’s SC mission. SAMIS improves the effectiveness, timeliness, and accuracy of data processing related to Air Force Materiel Command (AFMC) negotiations, acquisition, and physical delivery functions of international logistics support requirements.
C13.3.4.6. Case Performance Reporting System. DSCA (Office of Business Operations, Financial Policy and Regional Execution Directorate, Financial Analysis and Compliance Division (OBO/FPRE/FAC)) utilizes the Case Performance Reporting System (CPRS) to provide Congress, State, Department of Commerce, and DSCA with a DoD-wide view of FMS as well as other DoD and State sales programs information. DSCA (OBO/FPRE/FAC) uses the CPRS to gather monthly and quarterly materiel delivery data to produce unclassified and classified congressional reports. The system is sourced with monthly transactions received from IAs through DSAMS. Quarterly materiel delivery transactions are received from DIFS.
C13.3.5. Monitoring and Reporting. These IT systems are designed to monitor defense articles or services transferred by the USG to foreign recipients and verify they are being used in accordance with the terms and conditions of an applicable agreement. They also provide the means to fulfill USG monitoring and reporting requirements.
C13.3.5.1. Security Cooperation Information Portal. The SCIP provides web-based visibility of information about FMS and other key SC programs and processes by drawing upon data that is sourced from DSAMS case information and selected portions of case execution derived from MILDEP/IA systems (e.g., CISIL, MISIL, SAMIS, and the Case Tracking System (CTS)) in a standardized format. SCIP provides case information, regardless of which MILDEP/IA is managing the case and is a tool for foreign partners, customer agents (e.g., freight forwarders), and USG personnel with appropriate permissions.
C13.3.6. Education, Training, and Workforce. These IT systems provide the means for the SC community to manage and execute trainings and courses under SC authorities.
C13.3.6.1. Cornerstone on Demand. Cornerstone on Demand (CSOD) is a modular education-context Defense Security Cooperation University (DSCU) business management system that provides DSCA with customer-facing and administrative business management capabilities.
C13.3.6.1.1. DSCU’s mission to train, certify, and track the SC workforce requires a learning and workforce management system to support that effort. CSOD is a commercial-off-the-shelf (COTS) management system that includes learning and performance management modules. Through a partnership with the Defense Acquisition University (DAU) to implement an instance of CSOD within their license and support structure, DSCU leverages DAU expertise and contract support to provide a comparable modeled education/training, tracking, and certification management system. CSOD incorporates two modules that provide: 1) learning management, certification, registration, and business intelligence functionality, and 2) in-depth tracking and career planning, and improved management capabilities.
C13.3.6.2. GlobalNET. GlobalNET is an IT application to improve international outreach efforts and to strengthen collaboration among the DSCA Regional Centers (RCs), Office of the Secretary of Defense (OSD), and other DoD educational institutions. This program serves educators and students by allowing DSCA RCs to share information, collaborate on projects, and improve administrative activities with OSD, CCMDs, and DSCA. GlobalNET integrates student and knowledge management systems of DSCA RCs to provide them the ability to collaborate with foreign alumni and members of international organizations.
C13.3.6.3. Regional Center Personnel Activity Management System. Regional Center Personnel Activity Management System (RCPAMS) is the exclusive information system for entering and managing foreign military training data, reporting, and student logistics related to the courses, conferences, and events conducted by the DoD RCs. The web-based system is accessible 24-hours a day allowing RC users, who include RC staff and foreign partners, to process and track RC students during their interactions with the RCs, such as training events and alumni functions. RCPAMS is used by RC personnel to manage the operations and logistics of training events, provide a wide range of reporting, exchange data with other systems, facilitate tasking across RCs, provide and track two-way event-related communication to personnel.
C13.3.6.3.1. RCPAMS is the System of Record for the RCs' administrative information about individual students, their course enrollments, event attendance, and RC operations. It provides data to the Congressional Foreign Military Training Report (FMTR) (See Section C10.21.2.).
C13.3.6.3.2. RCPAMS requires Common Access Card (CAC) authentication to gain access. RCPAMS interfaces with the Security Assistance Network (SANweb) to access and share student activity data with DSAMS. Each RC is responsible for maintaining an independent instance of the common RCPAMS, and ensuring their particular system maintains conformity to the uniform process and reporting requirements.
C13.3.6.4. Security Assistance Network Web. SANweb is a portal through which Security Cooperation - Training Management System (SC-TMS) can be accessed. The SANweb is for use by SC offices, CCMDs, MILDEPs, IAs, DSCA, Defense Finance and Accounting Service (DFAS), DoD schoolhouses, DSCA RCs, and other organizations involved in SC.
C13.3.6.5. Security Cooperation - Training Management System. The SC-TMS resides within the SANweb and is used primarily by Security Cooperation Organizations (SCOs) and International Military Student Offices (IMSOs) to manage the SC training program for the foreign partner. SC-TMS enables SCOs and IMSOs to:
C13.3.6.5.1. View Standard Training Lists (STLs) that include training course information.
C13.3.6.5.2. View Training Military Articles and Services List (T-MASL) data.
C13.3.6.5.3. Enter IMS information required for DoD security vetting and human rights screening.
C13.3.6.5.4. Enter SCO and IMSO contact information.
C13.3.6.5.5. Create Invitational Travel Orders (ITOs) for IMS.
C13.3.6.5.6. View schoolhouse location information.
C13.3.6.5.7. Edit and view country Combined Education and Training Program Plans (CETPPs).
C13.3.6.5.8. SC-TMS capabilities also provide IMS vetting adjudication as well as IMS information, forms, and reports such as FMS and IMET program summaries. Training data is transferred daily to and from DSAMS through an automated interface process. Training data input by SCOs is included in the annual FMTR to Congress.
C13.3.6.6. Security Cooperation Workforce Database. Housed within the SANweb, the Security Cooperation Workforce Database (SCWD) provides the training status for the SC workforce. It contains SC positions around the world, organized by organization and funding source. SCWD is a shared management system between DSCA (DSCU) and the SC community. DSCA (DSCU) provides technical maintenance for the database and all training records. SCWD administrators from organizations in the SC workforce are responsible for managing the individual records for their organizations’ positions and personnel.
C13.3.7. Business Operations. DSCA manages IT systems and projects that provide the means to oversee and manage the health of the FMS Trust Fund and to enable the planning, budgeting, and accounting of Title 10 and Title 22 funding. Other IT systems and projects support DSCA’s physical security, facilities and maintenance, contracting, information technology enterprise services/support, and talent management.
C13.4.1. All DSCA-funded information systems and networks, as authorized by the DSCA Authorized Official, are governed by DSCA’s Cybersecurity Program. This program supports the Security Cooperation (SC) community through the latest technologies to ensure that security and privacy requirements are addressed and visible in all capability portfolios, across information technology (IT) life-cycle management processes, and DSCA-funded investment programs that incorporate IT. DSCA’s multi-tiered Cybersecurity Framework implements this program to protect U.S. interests, DSCA operational capabilities, and DSCA individuals, organizations, and assets.
C13.4.2. In addition to implementing the Cybersecurity Framework, the DSCA Cybersecurity Program supports the security assistance (SA) community by:
C13.4.2.1. Developing a DSCA-wide understanding to manage cybersecurity risks to SC assets, information systems, people, data, and capabilities.
C13.4.2.2. Implementing appropriate safeguards to ensure critical capabilities are delivered.
C13.4.2.3. Developing and implementing the required activities and capabilities to identify cyber events and incidents.
C13.4.2.4. Implementing the necessary activities and capabilities to take decisive action when a cybersecurity event or incident is detected.
C13.4.2.5. Developing and implementing the appropriate capabilities and activities to maintain, exercise, and refine plans to restore capabilities and services that were impaired in a cybersecurity event or incident.
C13.5.1. DSCA’s Data Management Program, under the purview of DSCA’s Chief Data Officer (CDO), was established in accordance with Department of Defense Instruction (DoDI) 8320.02, “Sharing Data, Information, and Technology (IT) Services in the Department of Defense” to provide the standards, requirements, and governances to make Security Cooperation (SC) data visible, accessible, and usable throughout the data’s lifecycle. Data is defined as a representation of facts, concepts, or instructions, such as text, number, graphics, documents, images, sound or video, in a form suitable for communication, interpretation or processing, which individually have no meaning by and in themselves. DSCA’s Data Management Program ensures that:
C13.5.1.1. Data standards, data services, and data specifications support IT interoperability, to include both the technical exchange of data and the resulting operational outcomes.
C13.5.1.2. Data is properly protected in accordance with applicable law, policy, data rights, and security classifications.
C13.5.1.3. Data architecture, guidelines, and general processes is developed and maintained using a whole-of-government approach and will have documented change control and configuration management protocols.
C13.5.1.4. Enterprise metadata and master data management provides visibility and consistent data usage across the SC enterprise.
C13.5.2. Data Governance. DSCA Data Governance provides the SC enterprise with the principles, policies, processes, frameworks, tools, and metrics needed to effectively manage data throughout the data lifecycle in accordance with the DoD Data Strategy.
C13.5.3. Security Cooperation Data Governance Board. Chaired by the DSCA CDO, and composed of representatives from across the SC community, the SC Data Governance Board (DGB) supports the development, approval, and compliance of DSCA and SC community data products and standards. The CDO, as the DGB Chair, supports the IT Governance Framework by providing DGB recommendations for leveraging data and best practices to the Portfolio Investment Review Board (PIRB) and the Strategic Investment Board (SIB).
C13.5.4. Data Council. The Data Council is internal to the DSCA Data Management Program and supports the development of enterprise-level products and standards as well as provides recommendations to the CDO for escalation to the SC DGB and the DSCA Chief Information Officer (CIO).
C13.5.5. Data Standards Baseline. DSCA established an SC data standards baseline to ensure compliance with DoD IT standards and the DoD IT Standards Registry (DISR). These standards are to be used by all SC system development and modernization activities funded by DSCA. Non-compliance with these standards may result in a reduction and/or termination of funding and resources. DSCA (Office of Business Operations, Information Management and Technology Directorate (OBO/IMT)) manages accessibility to the SC data standards baseline.
C13.5.6. Data Dictionary Specification. DSCA funded SC systems must utilize a common data dictionary specification to ensure consistent formatting and data descriptions necessary to facilitate collection of mandatory metadata within the SC data inventory. To ensure data dictionaries are standardized across the SC enterprise, SC information systems must utilize the DSCA data dictionary specification when developing and updating their data dictionaries. DSCA (OBO/IMT) manages accessibility to the DSCA data dictionary specification.
