Incorporated
Policy changes from this SAMM E-Change memo have been incorporated into the SAMM.
 | DEFENSE SECURITY COOPERATION AGENCY | 5/17/2019 |
MEMORANDUM FOR :
DEPUTY UNDER SECRETARY OF THE AIR FORCE FOR INTERNATIONAL AFFAIRS
DEPUTY ASSISTANT SECRETARY OF THE ARMY FOR DEFENSE EXPORTS AND COOPERATION
DEPUTY ASSISTANT SECRETARY OF THE NAVY FOR INTERNATIONAL PROGRAMS
DIRECTOR, DEFENSE CONTRACT MANAGEMENT AGENCY
DIRECTOR FOR SECURITY ASSISTANCE, DEFENSE FINANCE AND ACCOUNTING SERVICE-INDIANAPOLIS OPERATIONS
DIRECTOR, DEFENSE INFORMATION SYSTEMS AGENCY
DIRECTOR, DEFENSE LOGISTICS AGENCY
DIRECTOR, DEFENSE LOGISTICS INFORMATION SERVICE
DIRECTOR, DEFENSE LOGISTICS AGENCY DISPOSITION SERVICES
DIRECTOR, DEFENSE THREAT REDUCTION AGENCY
DIRECTOR, MISSILE DEFENSE AGENCY
DIRECTOR, NATIONAL GEOSPATIAL-INTELLIGENCE AGENCY
DEPUTY DIRECTOR FOR INFORMATION ASSURANCE, NATIONAL SECURITY AGENCY
DIRECTOR, DEFENSE TECHNOLOGY SECURITY ADMINISTRATION
SUBJECT :
End Use Monitoring (EUM) Focused Verification Checks (FVC) and Reporting Potential End Use Violations, DSCA Policy 19-04 [SAMM E-Change 419]
This memorandum revises the Security Assistance Management Manual (SAMM) Chapter 8 on EUM to establish requirements for Focused Verification Checks (FVC) and clarify reporting requirements for potential violations regarding the end use of U.S.-origin defense articles.
Focused Verification Checks (FVC) are a mechanism by which the Director, DSCA can proactively address issues that could lead to actual end-use violations. FVCs are ad hoc inspections of U.S.-origin defense articles directed at the discretion of the Director, DSCA, when concerns arise regarding their use, transfer, and physical security.
The revision also provides more detailed guidance on the requirements and process for reporting potential end-use violations to the DSCA EUM Team and to the Department of State.
The attached SAMM change will be included in Chapter 8 of the online version of the SAMM found on the DSCA Web Page as SAMM E-Change 419. For questions regarding this change, please contact the DSCA EUM Team at dsca.ncr.bpc.mbx.eum-helpdesk@mail.mil. For general questions about the SAMM, please contact Mr. Mike Slack, DSCA/SPP/SPI, at 703-697-9058 or e-mail: micheal.d.slack.civ@mail.mil.
Charles W. Hooper
Lieutenant General, USA
Director
ATTACHMENT :
As stated
CC :
AFRICOM
CENTCOM
EUCOM
NORTHCOM
SOUTHCOM
INDOPACOM
TRANSCOM
SOCOM
STATE/PM-RSAT
USASAC
SATFA
USACE
NAVSUP WSS
NETSAFA
TRADOC SATFA
AFSAC
AFSAT
DISCS
MARCOR IP
SCETC
USCG International Affairs (G-CI)
DSCA 19-04 - E-Change 419
End Use Monitoring (EUM) - Reporting Potential End Use Violations
Revise C8.5.1. as follows:
C8.5.1. EUM Visit Guidance. The Golden Sentry EUM program includes in-country visits. There are four types of EUM visits:
- Familiarization and Assistance Visits (FAV)
- Compliance Assessment Visits (CAV)
- Focused Verification Checks (FVC)
- Investigation Visits
Each visit is unique to the partner nation and equipment being assessed.
Add the following as a new section C8.5.4.:
C8.5.4. Focused Verification Checks (FVC). Focused Verification Checks (FVC) are ad hoc inspections of U.S.-origin defense articles for which there are concerns regarding their use, transfer, and physical security. FVCs are directed at the discretion of the Director, DSCA and provide the Director, DSCA greater visibility and real-time situational awareness of U.S.-origin defense articles. FVCs are a mechanism by which the Director can proactively address issues that could lead to actual end-use violations.
C8.5.4.1. Transmittal. DSCA will transmit FVC requests to SCOs through their assigned Combatant Command. The transmittal will identify the type, quantity, and location of U.S.-origin defense articles to be inspected and the date by which the verification must be completed. FVC requests may include one or more U.S.-origin defense articles at one or more locations.
C8.5.4.2. FVC Execution. SCOs will conduct FVCs in accordance with Routine- or Enhanced-EUM procedures based on the EUM-designation assigned to the U.S.-origin defense article(s) being checked. In some cases, DSCA personnel may conduct the FVC. FVCs are considered complete once SCOs have uploaded or submitted all required documentation in the SCIP-EUM database, as identified in C8.3. Routine EUM and C8.4. Enhanced EUM. As with any Routine- or Enhanced-EUM check, potential end-use violations must be immediately reported to DSCA and State through their respective EUM Potential End-Use Violation inbox (Unclassified: dsca.ncr.fo.mbx.eum-violations@mail.mil and PM-EUM-Incidents@state.gov; or Classified: dsca.ncr.fo.mbx.eum-violations@mail.smil.mil and PM-EUM-Incidents@state.sgov.gov ).
C8.5.4.3. Extensions. SCOs may submit a written request for an extension to complete an FVC to the DSCA EUM Program Manager through their assigned combatant command. Extension requests should include the proposed new completion date and a justification for the request.
Add the following as a new section C8.6.2.1. through C8.6.2.3.:
C8.6.2.1. Reporting. The President is obligated, pursuant to Arms Export Control Act Section 3(c)(2), to report end-use violations to Congress. The Department of State, with input from DoD, is the lead agency responsible for reporting end-use violations. All DoD personnel must report any suspected End-Use violations of U.S.-origin defense articles, including unauthorized access, unauthorized transfers, security violations, or known equipment losses, to the USG either through the SCO or directly to DSCA and State through their respective EUM Potential End-Use Violation inbox (Unclassified: dsca.ncr.fo.mbx.eum-violations@mail.mil and PM-EUM-Incidents@state.gov; or Classified: dsca.ncr.fo.mbx.eum-violations@mail.smil.mil and PM-EUM-Incidents@state.sgov.gov ). Any non-DoD personnel may also report suspected end-use violations directly to these same organizations or through the same email addresses.
C8.6.2.2. Reporting Requirements. A SCO must report a potential end-use violation, or submit an update to a previously reported potential violation, on the basis of information from any source, including a private person unaffiliated with the USG or a foreign citizen. Suspected end-use violation reports should include, to the maximum extent possible, the following information:
- The date(s) of the suspected violation.
- A description of the suspected violation to include: exact location, defense article(s) or service(s) involved, nature of the violation (non-approved use, unauthorized access/transfer or inadequate physical security).
- Date and description of corrective action(s), if any, taken by the partner nation.
- Contact information for the person initially reporting a potential violation (Name, grade and title (as applicable), phone number, email, etc.)
- If different from #4, contact information for the person reporting the violation to the DoD EUM Potential Violations email inbox and the State email inbox.
- Any other relevant information.
- End-Use Violation Incident number (An incident number will only exist if the report constitutes an update to a previously reported potential violation).
C8.6.2.2.1. When available, the incident number should always be included in the subject line of any updates as well as the update number, e.g. 1st Update, 2nd Update, etc. Reports involving classified information must be transmitted via a secure, classified network.
C8.6.2.2.2. Upon receipt of an incident report, State Department will take the lead on coordinating the U.S. Government response, which will include potential courses of action. When State receives information on potential end-use violations through its channels, it will share that information with DSCA.
Figure C8.F2. - Section 3 Violation Reporting Process
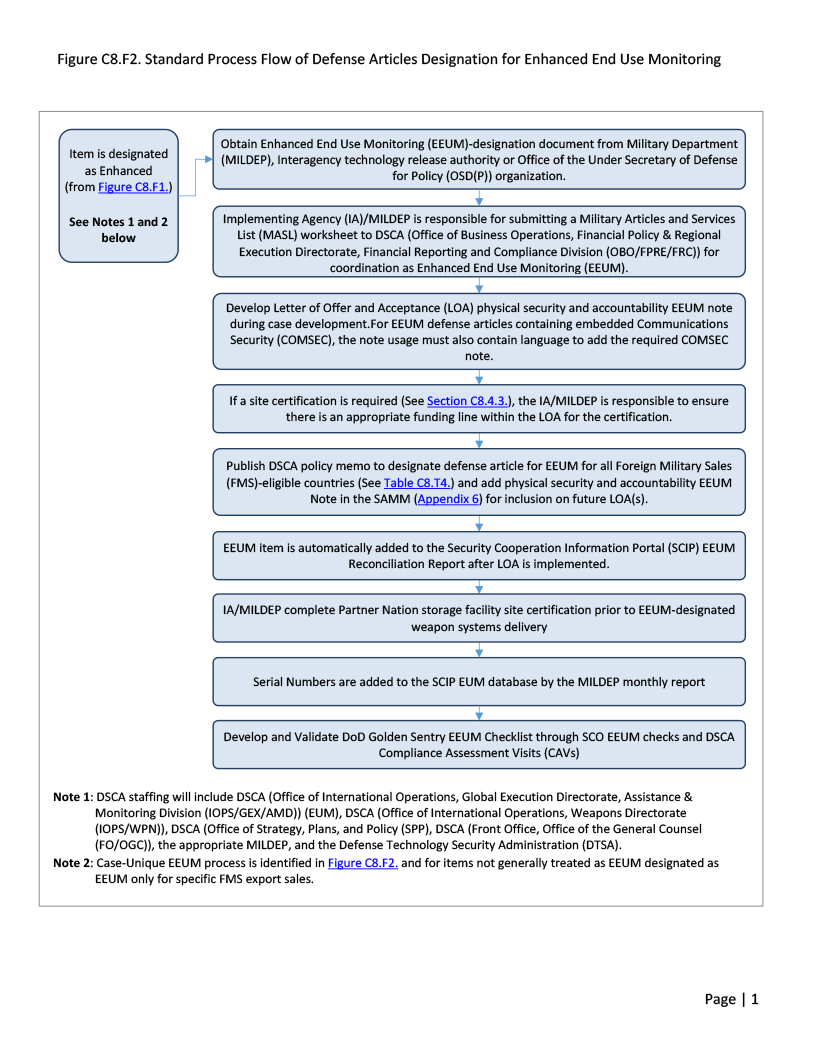
C.8.6.2.3. Roles and Responsibilities for Investigation of a Suspected End-Use Violation.
C8.6.2.3.1. SCO - Forwards reports received from other USG or non-USG personnel as well as any potential violations uncovered during Enhanced- or Routine- EUM checks to the appropriate DoD and State EUM Potential Violation email inboxes. Assists in collecting or obtaining additional information related to a potential EUM violation. Assists in the enforcement and application of consequences, as determined by the Department of State, resulting from confirmed end-use violations.
C8.6.2.3.2. DSCA/EUM - Monitors/manages the classified and unclassified DoD EUM Potential Violation email inbox. Maintains a master repository of reported potential end-use violations. Ensures the SCO and proper POCs at the CCMD are aware of all reported potential violations in their AOR. Assigns potential violation reports an incident tracking number. Assesses reports for completeness and credibility, and, when necessary, collects or obtains additional information. Assists in the enforcement and application of consequences, as determined by the Department of State, resulting from confirmed end-use violations.
C8.6.2.3.3. PM/RSAT - Serves as the primary USG authority for responding to reports of potential end-use violations, communicating to DoD the DOS investigation status of and other information related to potential end-use violations. Receives potential end-use violations and conducts investigations. In coordination with the diplomatic and security cooperation communities, determines the actions to be taken, if any, by the USG to address findings in the investigation reports. As necessary, reports findings to Congress.
- Renumber the current C8.F2. as C8.F3. and references as required.
